Although Raspberry Pi has much more powerful hardware if it is used as a VPN Router, it's wifi support and single LAN can be a problem to many. Also I found the current OpenWRT implementation for it can be flaky at times.
There are few OpenWRT supported travel routers on the market, and NEXX WT3020F is one of them.
Although OpenWRT can work as an OpenVPN client and has the luci-app-OpenVPN package to assist the configuration, I always find it too clumsy. This seems to change in versions after 18.6.2 (if you are 18.6.x, please follow this tutorial: https://blog.cavebeat.org/2018/02/vpn-tunnel-as-a-wan-interface-on-openwrt-lede-router/)
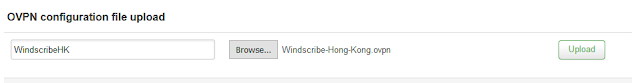
The luci-app-OpenVPN client in recent snapshots show that you can now configure the OpenVPN client by uploading an ovpn configuration file. This makes things so much easier!
To configure your OpenWRT router for OpenVPN, you
1) Upload the ovpn configuration file
2) Go to setting edit, and put in your credential in the auth-user-pass section box provided, and put the path of this "file" (see highlighed) next to the auth-user-pass option.
3) Set up the tunnelling (see my Raspberry Pi VPN Setup for steps), and you are ready to go!
3) Set up the tunnelling (see my Raspberry Pi VPN Setup for steps), and you are ready to go!
Update:
If you are using OpenWRT 18.6.x, please follow this tutorial. This tutorial is much simpler than many I found on the Internal. It shows you how to use ovpn to setup your VPN rather than transferring it setting using the luci-app-openvpn GUI.
https://blog.cavebeat.org/2018/02/vpn-tunnel-as-a-wan-interface-on-openwrt-lede-router/
Here are steps:
Transfer the ovpn file obtained from your VPN provider to /etc/openvpn
Here are the commands I used:
touch sigavpn_ny.ovpn
vi sigavpn_nv.ovpn
The first line creates an ovpn file, and the second line opens the file for editing. I transfer the content by simple copy and paste.
After pasting the contents, look for this line
auth-user-pass
Append this line with the path to the password file, e.g. /etc/openvpn/sigavpn_ny.auth
Now create the password file with the path you previously put in the ovpn file, e.g.
# assumed you are already in /etc/openvpn
touch sigavpn_ny.auth
vi sigavpn_ny.auth
The password file should have two lines. First line is your username, and the second line is your password.
Lastly, alter the openvpn file in /etc/config to link everything up, e.g.
config openvpn 'siga_vpn'
option enabled '1'
option config "/etc/openvpn/sigavpn_ny.ovpn"